- Compliance
- Project Management
How to ensure healthcare data security: principles to follow
The healthcare sector has undergone a significant transformation due to the development of IoT devices, web networks, and the accelerating process of digitization. These advancements facilitate the smooth flow of information, improve care quality, and speed up patient diagnoses. However, this digital revolution also poses challenges in terms of cybersecurity.
In this article, we will delve into the most critical threats and vulnerabilities, discuss the consequences of data breaches, explore the general principles of HIPAA and DiGA, and present best practices to guarantee a high level of heatlhcare data security.
Navigating HIPAA and DiGA Regulations
Securing healthcare data demands strict compliance with regulations such as HIPAA (Health Insurance Portability and Accountability Act) and DiGA (Digitale Gesundheitsanwendungen). These regulations are respectively applicable in the USA and Germany, and they delineate how service providers and healthcare organizations should handle patient data to ensure confidentiality.
Violations of HIPAA and DiGA can result from errors such as insufficient security controls, the absence of audits, incorrect risk assessments, or inadequate patient data protection. The consequences can be severe, ranging from substantial fines and lawsuits to regulatory oversight or even imprisonment.
For instance, Anthem had to cough up $115 million due to a patient data breach, Memorial Healthcare System settled for a $5.5 million agreement for inadequate data protection, and NY-Presbyterian Hospital incurred a $4.8 million fine for carelessly sharing patient data online.
These cases underscore the seriousness of failing to comply with applicable regulations.
Best Practices for Fortifying Healthcare Data Security
To safeguard patient data and uphold its integrity, organizations should put into action a range of principles. Here are a few of them:
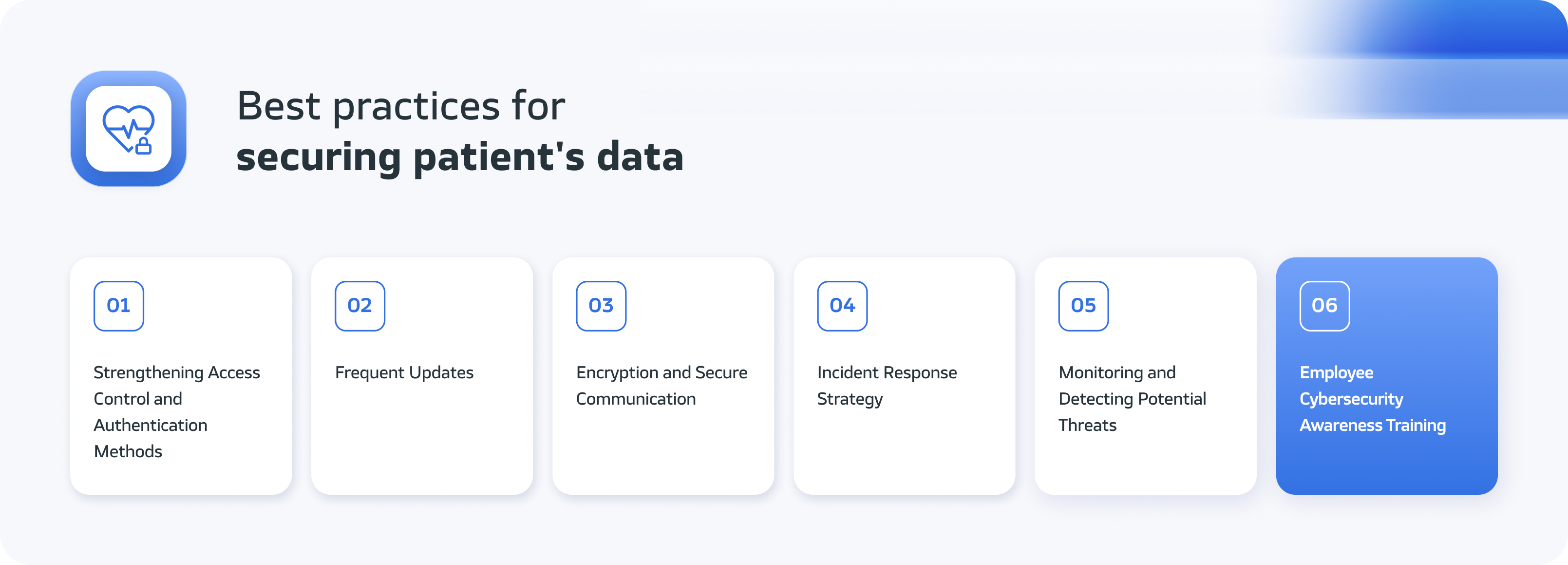
Strengthening Access Control and Authentication Methods
A fundamental aspect of healthcare security is establishing robust access control and putting in place proper authentication protocols. This ensures that only authorized individuals can access specific devices and resources, thus mitigating the risk of unauthorized access and potential security breaches.
Two-factor authentication (2FA) and multi-factor authentication (MFA) play a crucial role in a robust security strategy. They require users to provide more than one form of identification before gaining access. Keeping permissions up to date is also crucial.
Additionally, implementing the Principle of Least Privilege (PoLP), which dictates that individuals should have access only to the minimal resources and permissions necessary to perform their tasks, can further enhance security.
Organizations should also contemplate implementing a comprehensive security policy that mandates password changes and access verifications.
Frequent Updates
The healthcare sector faces constant challenges from ever-evolving threats. To meet the highest security standards, companies operating in this sector should adhere to several principles.
Patch Management: Effectively managing patches is critical for quickly addressing known vulnerabilities and preventing their exploitation by third parties. This ensures that devices and software remain up-to-date and secure.
Proactive Vulnerability Management: In addition to responding to known vulnerabilities, healthcare organizations should employ proactive strategies to detect potential weaknesses in security systems.
Regular penetration testing helps unearth hidden vulnerabilities before they can be exploited. Leveraging vulnerability scanners like OpenVAS can automate this process, allowing for concurrent host, vulnerability, and custom port list scans.
Automated Patch Management: Manual updates can be overwhelming, especially with a large number of devices. Using automated patch management simplifies the process by automatically detecting and applying patches to managed devices and systems.
It’s important to understand that different IT infrastructure areas have distinct procedures and methods for updating, including operating systems, device software, and web applications. When discussing automated patch management, these differences should be considered, with each area requiring an adjusted approach.
Operating Systems: OS patch management involves identifying available updates, downloading them, and installing them on devices. Organizations must configure appropriate update schedules to prevent system disruptions.
Device Software: Devices like routers, printers, or IP cameras also require software updates to enhance security and functionality. Administrators can remotely update firmware, and devices may automatically check for necessary patches.
Web Applications: Web applications need regular updates as well. Automated patch management in this context involves automatically deploying new application versions and monitoring and responding to known vulnerabilities in real time.
Encryption and Secure Communication
Utilizing encryption and secure communication protocols within systems is essential to maintain the proper security of patient data.
Encryption involves transforming data into an encoded format that can only be decrypted using the appropriate decryption key. Encryption ensures that patient data and other sensitive information remain confidential during transmission.
Even if intercepted by unauthorized entities, the information remains unreadable and secure. Recommended protocols include Transport Layer Security (TLS) and Secure Sockets Layer (SSL), commonly used in web browsers, email, and IoT devices that handle sensitive data.
Furthermore, for systems that only communicate internally without external network access, establishing an internal VPN network is advisable.
Incident Response Strategy
In the realm of healthcare cybersecurity, preparedness for unforeseen events is paramount. A well-defined incident response plan is invaluable. It’s a comprehensive framework that outlines an organization’s response to specific events, such as the discovery of a system vulnerability.
Incident Identification: First, clear procedures must be established, and employees should be trained to swiftly identify security-related incidents.
Classifying incidents according to a predefined hierarchy allows for prioritization. Information security management requires the identification of incidents in accordance with the ISO/IEC 27043 standard. Organizations should have clear procedures and provide training to ensure the rapid detection of potential threats.
Additionally, having a dedicated incident response team with clearly defined roles for both internal and external stakeholders is essential.
Response Plan: A security incident response plan outlines the necessary steps to take after an incident is detected. The first step is to isolate the issue to prevent further damage. Subsequently, the source of the threat should be removed, and normal system operations restored.
Monitoring and Detecting Potential Threats
Cyber threats are becoming increasingly complex, necessitating constant vigilance. Implementing robust monitoring systems enables the quick detection of unusual and suspicious activities that may indicate a security breach.
Advanced techniques like behavioral analysis and machine learning can enhance threat detection by identifying abnormal behavioral patterns and sending alerts when deviations from the norm occur.
Additionally, leveraging external services such as Cloudflare, which continually updates a database of potential threats and monitors traffic, can be beneficial.
Employee Cybersecurity Awareness Training
Healthcare employees play a crucial role in protecting patient data. They often serve as the first line of defense against cyberattacks, as they interact with various devices and systems that store and transmit sensitive information.
Therefore, training and educating employees in cybersecurity awareness are essential to prevent potential threats. Some important topics they should be familiar with and practice include creating strong passwords, keeping software updated, and exercising caution.
Training healthcare employees in cybersecurity and traditional security practices promotes a sense of responsibility and duty toward data security, increasing the trust and confidence of patients and partners.
These efforts encompass protecting data from both cyberattacks and threats related to paper document theft or unauthorized access to physical data carriers. All these aspects are critical for maintaining security in healthcare.
 Key Takeaways
Key Takeaways
Ensuring healthcare data security and compliance with the law requires proactive efforts. In today’s interconnected world of healthcare, mere access control is not enough.
Data encryption, threat monitoring, and a comprehensive cybersecurity strategy are also necessary. While these measures may not yield immediate visible returns, they shield us from incidents that can significantly impact business continuity.
If you are seeking assistance in developing HIPAA-compliant software, Blurify is a trusted partner. As an experienced company specializing in HIPAA and DiGA-compliant software development, we have created solutions like LifeTraq.
This interactive behavioral platform offers comprehensive support for individuals facing challenges and is utilized by government agencies, correctional facilities, addiction treatment centers, and educational institutions in the USA, ensuring full HIPAA compliance.
We have also created Hurricane, a comprehensive casino management platform with an MGA license. To enhance security, we have implemented a comprehensive behavior analysis system, which sends notifications when suspicious behavior is detected.
Additionally, we continuously monitor and test our application, preventing errors and optimizing its performance. Our team has established a secure and scalable infrastructure based on AWS.
If you prioritize the security of your patients’ data and want to learn how we can assist you, feel free to reach out to us and engage with our team of experts. Together, we can create a cybersecurity strategy that safeguards patient data and elevates healthcare quality.