- Compliance
- Development
7 Best Practices to Keep Your App HIPAA Compliant
Digitization of the healthcare industry has created opportunities worldwide, with more than 350,000 healthcare apps now available in app stores. According to the GVR Report cover Digital Health Market Size, Share & Trends Report, the global health app market was valued at $38.2 billion in 2021 and is expected to grow at a compound annual growth rate (CAGR) of 11.8% between 2022 and 2030.
The main factor driving the app market is the increasing awareness of users concerned about improving their overall health and the vast availability of smartphones worldwide. Today, thanks to apps, many healthcare services have become more accessible. Such solutions make our lives easier with quick appointments, instant access to medical records, and convenient billing options.
So creating healthcare apps is a viable idea. However, you need to consider some essential aspects that will help you create a functional solution that complies with applicable laws. To build a healthcare app that interacts with electronically protected health information (ePHI), you should pay special attention to HIPAA law.
Table of Contents
What’s HIPAA compliance?
HIPAA (Health Insurance Portability and Accountability Act) is a U.S. federal law that is one of the cornerstones of compliance and healthcare cybersecurity. Hospitals, insurance companies, and healthcare providers must follow the HIPAA compliance checklist to protect private and sensitive patient data. The act sets security standards and privacy requirements for managing personally identifiable medical and health data.
Examples of healthcare and health-related applications that must be HIPAA-compliant are:
- Telemedicine or private messaging apps
- EHR apps
- Healthcare apps that collect data for or communicate with healthcare providers
- Applications that collect medical records/lab results
- Patient monitoring apps or medication compliance apps (if connected to physicians)
In addition to the security of PHI, HIPAA improves healthcare efficiency. For example, it allows various hospitals to exchange electronic medical records (EMRs) remotely and without paperwork. In addition, it helps employees transfer insurance when they change jobs.
What data does the HIPAA cover?
Protected health information (PHI) and electronically protected health information (ePHI) refer to any patient-identifiable data contained in medical records, including, e.g.:
- name,
- address,
- date of birth,
- device identifiers,
- email addresses,
- biometric, laboratory, or imaging results,
- medical history,
- payment information.
In contrast, HIPAA does not apply to primary health indicators (unless those indicators uniquely identify the patient), as they are considered non-identifiable data.
Who needs HIPAA compliance?
HIPAA must be complied with by all companies and employees who work with protected health information. This includes organizations and medical professionals who have direct contact with personal information.
Some examples are:
- Healthcare providers (hospitals, clinics, nursing homes, pharmacies, physicians, psychologists, and dentists),
- Healthcare plan providers (insurance companies, healthcare organizations, government healthcare programs, and military healthcare programs),
- Healthcare clearing houses (entities that transfer and process data between providers and health plans, such as community management systems and billing services)
HIPAA compliance is a must for healthcare-related organizations and partners. This article provides a checklist to ensure your software is HIPAA-compliant and steps to take to stay HIPAA-compliant.
7 tips on what makes software HIPAA-compliant
You must configure the software to comply with HIPAA guidelines, which address several areas of patient data protection. They include detailed procedures for data protection and security breach notification. When developing healthcare software, it is essential to comply with the technical safeguards of HIPAA and the administrative and physical aspects of the act.
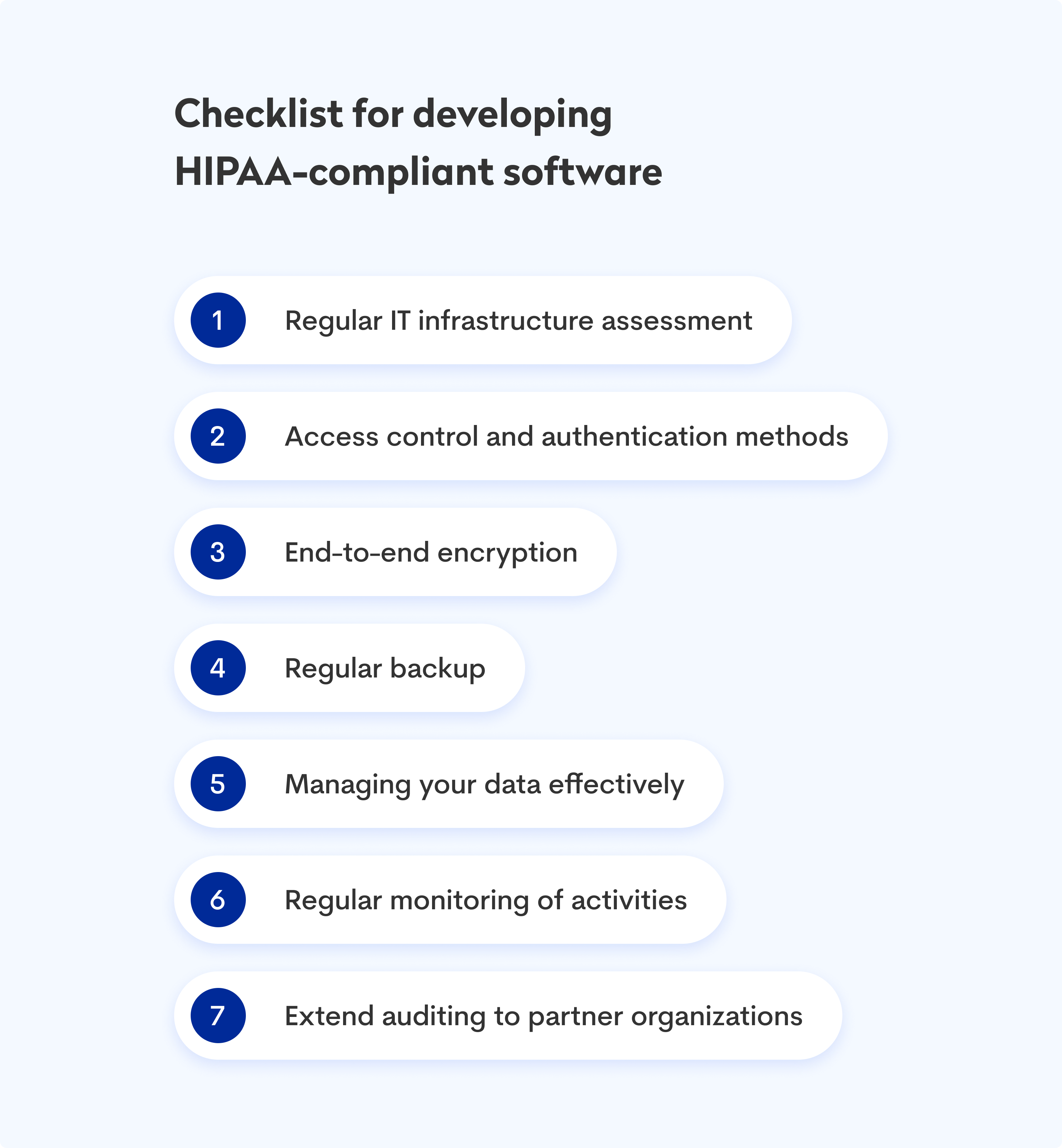
Here is a checklist for developing HIPAA-compliant software:
1. Regular IT infrastructure assessment
To prevent HIPAA violations, you should conduct regular internal audits. Evaluating the extent to which policies your organization follows and what contingency procedures are in place will help you assess how your software addresses HIPAA compliance. This process goes beyond a simple risk analysis of your security measures – you should audit your IT infrastructure, administrative structure, policies, and agreements with business partners.
After completing the audit process, you should know the following:
- Where are your critical business data and PHI stored?
- If you share PHI with third parties, is this done following HIPAA? Have you reviewed access logs for electronic databases?
- Does your software log all login attempts?
- Have there been security incidents, and how have they been prevented?
- Test the security mechanisms that should work in case of a data security breach, what data management policies and procedures are in place,
- What are the risks and potential vulnerabilities in your electronic records?
2. Access control and authentication methods
The goal of HIPAA is to prevent the misuse of data. Therefore, those dealing with PHI should see only the “minimum of what is necessary” to perform their duties. With access control, you allow different levels of access to patient data, thus reducing the potential misuse of information.
Regarding access control in HIPAA-compliant software, it is essential to mention authentication methods. What are ways to strengthen cybersecurity?
- Secure password policies. Ideally, passwords should contain at least eight characters (including letters, numbers, and special symbols) and exclude vocabulary or frequently used combinations.
- Multi-component authentication. This allows users to access the system only after entering additional verification methods. These could be biometrics, face ID, one-time generated passwords sent to their devices, or email.
- Enable automatic logout. This automatically terminates sessions after a specified time or period of inactivity. Shorter sessions protect health data because there is no time to tamper with it.
- Antivirus and firewall protection. Intrusion detection tools can detect suspicious activity and temporarily block user accounts to prevent data breaches.
- Extend security measures to mobile devices
- Use secure Wi-Fi networks or VPN software.
3. End-to-end encryption
HIPAA guidelines for encryption are stringent. Under the act, ePHI must be encrypted both at rest and during transmission.
Encryption means converting data into an unreadable format that can only be unlocked with a security key. As a covered entity, you should invest in robust cryptographic protocols (PGP, IPsec, SSH, and TLS/SSL) to secure your data. Depending on the size of your organization, you may also want to encrypt databases, cloud servers, and employee mobile devices.
4. Regular backup
HIPAA also specifies a breach notification rule. When an emergency occurs, such as a server failure, natural disaster, data corruption, or ransomware that prevents access to critical files, specific HIPAA-compliant procedures should be followed.
Among other things, you should configure HIPAA-compliant software to back up data regularly. It should also be able to restore critical business data and PHI in emergencies.
To improve disaster recovery and backup, you should:
- Develop policies for backing up PHI and other critical data
- Back up medium and high-risk data daily
- Store data backups in a secure facility (locally or remotely)
- Review your storage systems regularly (monitor logs, analyze system downtime and detect backup data errors)
5. Manage your data effectively
You should minimize the amount of sensitive data you store in your systems. Typically, PHI records may contain duplicate data, old backups, and medical records of previous patients. To do this, it’s a good idea to use programs that automatically scan disks, databases, and archives for unused data. In addition, data logs that contain protected health data should be deleted.
Data should also be deleted from portable storage devices such as USB flash drives, laptops, network cards, and smartphones. HIPAA-compliant software should store data in a secure storage environment. This usually includes a physical data storage location, which must be within the US.
6. Monitor activities regularly
HIPAA-compliant software must keep records of PHI-related activities for six years and record all login attempts, including failed logins and logins from unusual devices and locations. It is essential to automate activity monitoring.
7. Extend auditing to partner organizations
Healthcare-related companies rarely use self-developed HIPAA-compliant software. More often than not, healthcare-related organizations often work with partner companies to improve their services.
It is essential to know that business partners are also subject to HIPAA. Before working together, organizations must sign a business associate agreement. It should specify how PHI data is used by partner organizations, such as IT consultants or software and hosting providers.
 Work with an experienced HIPAA provider
Work with an experienced HIPAA provider
We know our HIPAA responsibilities and understand the importance of data security being processed by healthcare organizations. We also have experience in building health-related applications. For example, we built a Life Track app for a client in the US; we secured all user data concerning HIPAA. You can read more about the project here.
Finding the right software vendor that understands the complexities of data security can be time-consuming, but it brings benefits. Ensuring that all aspects of HIPAA are met will improve safety and help prevent costly data breaches.
Software prepared in this way will consider all HIPAA regulations, thus helping the company avoid regulatory penalties resulting from non-compliance.